My Laptop Is Restarting Again and Again Windows 10 With Trojan Virus
What is Trojan:Win32/Ymacco?
Ymacco Trojan is a piece of malware that can open backdoors and expose users to malicious websites

Trojan:Win32/Ymacco is a is a highly dangerous cyber infection that aims at injecting malicious scripts on the infected machines, downloading other unsafe programs, manipulating organization's performance, rerouting users' traffic to compromised websites, and more. In short, it can initiate various risk-posing performances on the host machine, so an ASAP removal is recommended.
This trojan[1] has been designed in a sophisticated manner, which is why information technology is capable of infecting machines stealthily via spam emails, pirated software, cracks, and similar content. Upon installation, it starts running malicious processes, ane of the most prominent of which is Uwgcset.exe. Usually, this process is highly obfuscated to prevent detection. Nevertheless, a full scan with a professional AV tool usually ends up alarm users virtually the Trojan:Win32/Ymacco.AAC9, Win32/TrojanDownloader.Delf.CYB, Trojan.GenericKD.43360621, and similar detection.
Unfortunately, the Ymacco virus is extremely deceptive equally it does not requite its presence straightforwardly. It can hide in the organization for quite a while unnoticed until the user spot high CPU usage by suspicious files, unfamiliar files within random folders, web-browser redirects to sites similar z.whorecord.xyz, a.tomx.xyz, pushwelcome.com, pushtoday.icu, and others. Malware like this can cause serious issues, such as spyware or ransomware infiltration, so make sure to remove the Trojan without a delay.
| Name | Ymacco Trojan |
| Type | Trojan |
| Danger | This trojan poses a gamble to the users of infected auto past initiating regular redirects to infected web domains, running malicious processes in the background, and downloading other malware to the system |
| Detection |
|
| Symptoms | The Trojan runs malicious processes in the background and triggers high CPU consumption. Besides, it may hijack web browsers and redirect the traffic to sites infected past malicious scripts |
| Removal | Malicious files go hidden in diverse arrangement locations and often disguised under legitimate Windows files/processes. Therefore, a total system scan with a professional AV tool is required for the proper Ymacco trojan removal |
| Fixing the damage | A scan with Reimage Intego tool is recommended since such tools like PC repair or system applications tin repair the afflicted organization'south settings, files, and processes. Total optimization is required to prevent issues in the time to come |
This trojan is oftentimes dubbed as Trojan:Win32/Ymacco.AAC9 on the basis of the AV detection brought by Windows Defender. Nevertheless, it's internationally known as the backdoor or trojan virus due to the traits that information technology has.
- The malicious trojan loader Uwgcset.exe infiltrates machines without existence noticed every bit a component of a malicious spam email zipper or pirated software similar cracks or keygens;
- Upon infiltration, it extracts the trojan package and starts running various malicious entries on the Startup and Task Director;
- It misuses CPU, which is why the organisation's performance decreases significantly;
- It aims at weakening the system's functioning to open the backdoor and enable access to other malicious software.
- It creates persistence to avoid detection and removal. Often the processes of AV programs are disabled.
- The Ymacco Trojan virus can inject malicious scripts within web browsers to open malicious websites;
Experts from Virusai.lt[3] claim that a regular organization scan with a reputable AV engine is a must to ensure that the system is virus-costless. Go on in mind that Trojans like the Ymacco virus are difficult to discover considering they practice not manifest themselves easily, so no scanning the machine on regular basis can mean a long persistence to the virus.
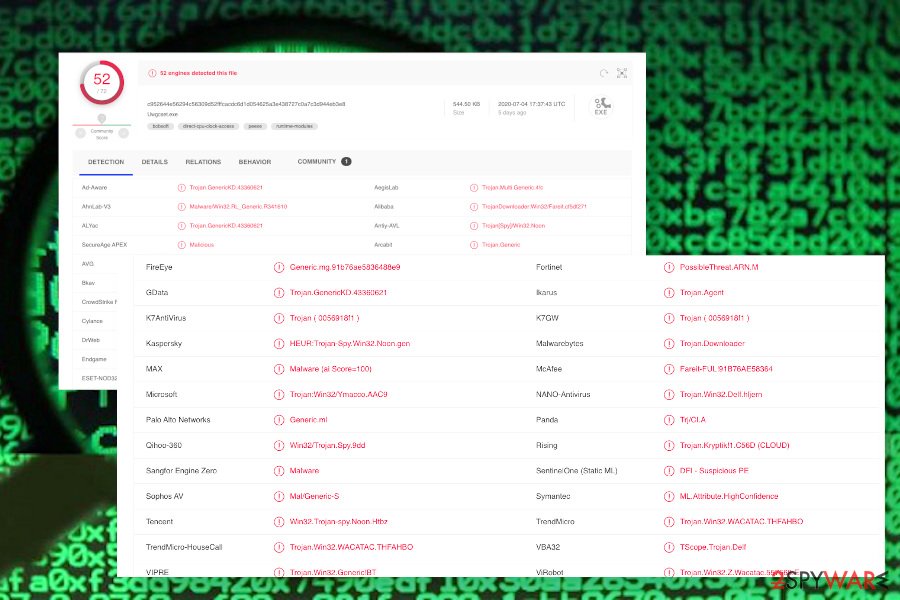
At the moment, a successful Ymacco trojan removal tin be initiated with 52 about reputable AV tools as they have crucial updates required for the detection of this pest. Note that the detection may differ regarding the application that you are using, so if yous want to exist clear if this particular trojan is hiding on your machine, y'all tin can check the VirusTotal provided detection names for it.
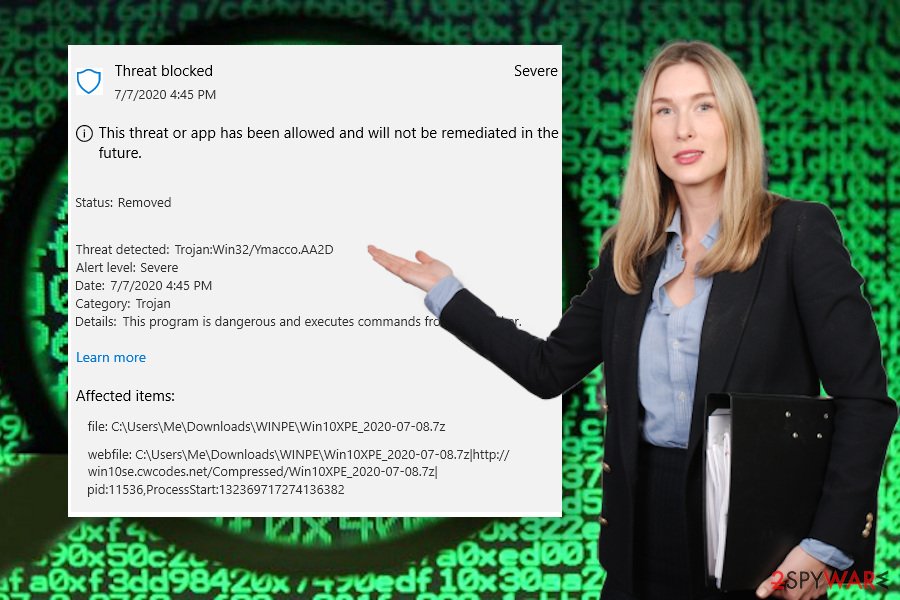
The good news is that the virus is not a spyware or banking trojan. It ways that it does not seek to steal your passwords or other credentials. It's primary task – weaken PC's security and increment vulnerability. After that, it exposes the user of an infected motorcar to the malicious domains, thus posing a high-adventure of malware downloads.
The bad news is that Ymacco trojan redirects can expose you to sites like z.whorecord.xyz, a.tomx.xyz, and others that are infamous for click-to-download malware distribution, infected software updates, click-bait ads, and other social engineering strategies.
Therefore, make sure to remove Ymacco Trojan every bit soon as possible. For this purpose, accept advantage of a powerful anti-virus plan and run its browse later restarting Windows into Safety Style with Networking.
As nosotros've already pointed out, a scan with an AV engine will not repair damaged system files. Thus, tight after the Ymacco virus removal, download Reimage Intego or similar repair tool and set information technology to set up all detected system issues.
Malicious code disguised nether file attachments tin can deliver trojans
The source of trojans cannot be specified because at that place are many. Criminals are using diverse techniques to make people slip on downloading malicious entries to their machines, and then the only precautionary measure is to exist careful when browsing online and keeping the motorcar fully protected past AV programs.
Even so, there are several methods that are known to exist the master trojan download sources. First of all, malicious codes are ofttimes hidden in spam email attachments. People may go fake email letters that supposedly contain financial data, receipts, invoices, order confirmations, and so on. Such emails may exist professionally crafted, though usually, they contain grammar, typo, and logic mistakes.
Autonomously from spam, people may be tricked into downloading trojans past downloading illegal content from P2P networks, torrenting sites, or other pirating sources. Hackers can easily inject malicious scripts into various cracks, keygens, tertiary-party games, etc.
Trojans are as well often distributed via infected links that people receive on social media. For instance, the well-known Facebook virus has been, and probably still is, the about successful malware distribution campaign. Therefore, do non trust suspicious content even if it comes from a trusted source.
Remove Trojan:Win32/Ymacco to protect the organisation from malware
There is a sole technique that is fully functional in dealing with viruses like Ymacco trojan. That's a thorough organisation scan with a robust anti-malware tool. Since this virus is highly dangerous in its nature as information technology poses a take chances to the user'south privacy and the system's security, information technology has to be fully eliminated.
Employing a professional person anti-malware for Ymacco trojan removal gives the advantage of cleaning other cyber infections at the same time. If you are not sure when the machine has been infected, there's a adventure that it has been running for a long time already and might accept downloaded a agglomeration of malicious files.
Rely SpyHunter 5 Philharmonic Cleaner or Malwarebytes tools for checking the system and performing a full Ymacco trojan removal. If you cannot launch the security tool, try to restart Windows into Safe Way with Networking (a guide provided below). Finally, practice not underestimate the need for the system's optimization. Download Reimage Intego and scan the machine to restore all files that the trojan might accept damaged or removed.
Manual removal using Safety Style
The Trojan:Win32/Ymacco.AAC9 detection is a signal that the system is infected with a Trojan and has to be cleaned to prevent various bug. For this purpose, restart the machine into Safe Mode and run a full arrangement browse every bit explained beneath:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to exist performed correctly (if vital arrangement files are removed or damaged, it might event in full Windows compromise), and information technology besides might accept hours to complete. Therefore, we highly advise using the automatic method provided higher up instead.
Step 1. Access Safe Manner with Networking
Manual malware removal should be best performed in the Safety Mode surround.
Windows vii / Vista / XP
- ClickFirst > Shutdown > Restart > OK.
- When your computer becomes active, start pressingF8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until y'all see the Advanced Boot Options window.
- SelectSafe Mode with Networking from the listing.

Windows ten / Windows 8
- Right-click on Commencement button and select Settings.

- Scroll down to option Update & Security.

- On the left side of the window, selection Recovery.
- Now gyre downwards to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Printing Restart.
- Now press v or click 5) Enable Safe Fashion with Networking.

Footstep 2. Shut downwardly suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you demand to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Whorl down to Groundwork processes section, and expect for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and option End Task.

- Delete the contents of the malicious folder.
Pace 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Correct-click on the suspicious program and pick Disable.

Step four. Delete virus files
Malware-related files can be found in various places within your estimator. Hither are instructions that could help you discover them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main bulldoze by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Make clean up system files.

- You tin can also look for other malicious files subconscious in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Trojan:Win32/Ymacco using System Restore
Finally, you should always retrieve about the protection of crypto-ransomwares. In order to protect your calculator from Trojan:Win32/Ymacco and other ransomwares, employ a reputable anti-spyware, such as Reimage Intego, SpyHunter five Combo Cleaner or Malwarebytes
The regime has many issues in regards to tracking users' data and spying on citizens, so you should have this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
Yous can choose a dissimilar location when you go online and access whatever material you desire without detail content restrictions. You tin can easily enjoy internet connection without any risks of being hacked by using Private Net Access VPN.
Control the information that can be accessed by government any other unwanted political party and surf online without beingness spied on. Even if you are not involved in illegal activities or trust your pick of services, platforms, be suspicious for your own security and have precautionary measures by using the VPN service.
Computer users tin can endure from data losses due to cyber infections or their own faulty doings. Ransomware tin can encrypt and hold files hostage, while unforeseen ability cuts might cause a loss of important documents. If y'all take proper upwards-to-date backups, you tin can easily recover after such an incident and get back to work. Information technology is also as important to update backups on a regular basis so that the newest data remains intact – you can set up this process to be performed automatically.
When you have the previous version of every important document or project yous tin avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Utilise Data Recovery Pro for the data restoration process.
Source: https://www.2-spyware.com/remove-ymacco-trojan.html

Postar um comentário for "My Laptop Is Restarting Again and Again Windows 10 With Trojan Virus"